Monday 7 October 2013
Friday 12 July 2013
Microsoft Office Outlook 2007
Microsoft Office Outlook 2007
- Start Outlook.
- On the Tools menu, click Account Settings.
- Click New.
- Click Microsoft Exchange, POP3, IMAP, or HTTP, and then click Next.
- In the Auto Account Setup dialog box, click to select the Manually configure server settings or additional server types check box, and then click Next.
- Click Internet E-Mail, and then click Next.
- In the Server Information section, select IMAP for Account Type.
- In the Your Name box, enter your name exactly as you want it to appear to recipients.
- In the E-mail Address box, type your e-mail address.
- In the User Name box, type your account name.
- In the Password box, type your password.
- In the Incoming mail server box, type the name of your IMAP4 server .eg imap.gmail.com like this will be your imap server
- In the Outgoing mail server (SMTP, eg. smtp.gmail.com) box, type the name of your SMTP server.
Note IMAP4 is a retrieval protocol. You must have SMTP to send your messages. - Click Next after you have completed entering this configuration information, and then click Finish.
Wednesday 12 June 2013
Free Sms send and get mobile recharge
Send free sms and get mobile Recharge .
its true friends. just sand sms and earn mobile recharge.
click here for visit or sand sms.
Send free sms
its true friends. just sand sms and earn mobile recharge.
click here for visit or sand sms.
Send free sms
GET FREE MOBILE RECHARGE
Hi, friends.
I visited this crazy site called 'Laaptu'
This site gives Free Mobile Recharge to all its users.
Play quiz, guessing game and get recharge in return.
I got joining bonus, you can join here
Have fun at Laaptu
~~visit site ~~ click here to visit site
free mobile Recharge
I visited this crazy site called 'Laaptu'
This site gives Free Mobile Recharge to all its users.
Play quiz, guessing game and get recharge in return.
I got joining bonus, you can join here
Have fun at Laaptu
~~visit site ~~ click here to visit site
free mobile Recharge
Wednesday 3 April 2013
How to setup BSNL Broadband connection for nokia siemens network
Have you bought a new BSNL broadband connection?
Are you worried, how to setup your BSNL broadband connection first time?
Then you are most welcome.....!!
I have written this after buying my nokia-siemens network type of BSNL-BROADBAND connection, but it will work for others also.
First of all, what you have to do is to connect your telephone line to the modem and wait for about a minute or so that the ADSL LED (green light) on the modem gets steady means constant lighting.
Now connect your computer/laptop to your modem
You will see a similar screen asking | |||||
CLICK ON RESTART.
You will see your window like this and when you click on ADSL and then
You will see your window like this and when you click on ADSL and then
When you will click on wan (wide area network),
Now click on Lan(local area connection)
And then enable DHCP Server and then start ip address and end ip address and leased time as shown in the picture below:
Now for DSL setting:
You are almost done. Now click on save/reboot button:
In the case you have done something wrong, you have option of setting everything as factory default.
Now you are done with the ADSL
Your next task is to see for wireless setting of BSNL Broadband connection.
Enable wireless and change number of maximum user ac to your wish, if you set it to 4, only four clients will be connected and 5th one will not be able to connect to your network:
When you click on advanced button, you will have various options
Lastly, if you click on station info, you will see as the screenshot, refresh it for current status.
Congratulation!!!
You have completed your setup of BSNL Broadband connection.
Now open your browser and enjoy surfing.
NAT (Network Address Translation)
NAT (Network Address Translation)
Primarily NAT was introduced to the world of IT and networking due to the lack of IP addresses, or looking at it from another view, due to the vast amount of growing IT technology relying on IP addresses. To add to this, NAT adds a layer of security, by hiding computers, servers and other IT equipment from the outside world.
How NAT works
When computers and servers within a network communicate, they need to be identified to each other by a unique address, in which resulted in the creation of a 32 bit number, and the combinations of these 32 bits would accommodate for over 4 billion unique addresses, known as IP address. This was named IPv4, and although over 4 billion addresses sounds a lot, it really is not considering how fast the world of computers and the internet has grown.
To circumvent this problem, a temporary solution was produced known as NAT. NAT resulted in two types of IP addresses, public and private. A range of private addresses were introduced, which anyone could use, as long as these were kept private within the network and not routed on the internet. The range of private addresses known as RFC 1918 are;
Class A 10.0.0.0 - 10.255.255.255
Class B 172.16.0.0 - 172.31.255.255
Class C 192.168.0.0 - 192.168.255.255
NAT allows you to use these private IP address on the internal network. So within your private network you would assign a unique IP address to all your computers, servers and other IP driven resources, usually done via DHCP. Another company can use the same private IP addresses as well, as long as they are kept internal to their network. So two companies maybe using the same range of IP addresses but because they are private to their network, they are not conflicting with each other.
However when internal hosts do need to communicate to the public network (Internet) then this is where a public address comes into the equation. This address usually purchased from an ISP is a routable public address everyone can see, which would represent your network gateway. This public address would be unique, no one else would use this address.
Now getting to the point; When a host on the internal network with an internal IP address does need to communicate outside it's private network, it would use the public IP address on the network's gateway to identify itself to the rest of the world, and this translation of converting a private IP address to public is done by NAT. For example a computer on an internal address of 192.168.1.10 wanted to communicate with a web server somewhere on the internet, NAT would translate the address 192.168.1.10 to the company's public address, lets call this 1.1.1.1 for example. so that the internal address is identified as the public address when communicating with the outside world. This has to be done because when the web server somewhere on the internet was to reply to this internal computer, it needs to send this to a unique and routable address on the internet, the public address. It can not use the original address of 192.168.1.10, as this is private, none routable and hidden from the outside world. This address, of 1.1.1.1 would be the address of the public address for that company and can be seen by everyone. Now the web server would reply to that public address, 1.1.1.1. NAT would then use its records to translate the packets received from the web server that was destined to 1.1.1.1 back to the internal network address of 192.168.1.10, and though the computer who requested the original info, will receive the requested packets.
Now you can obviously see the two benefits of NAT. Firstly it would save on the IP addresses we use, as every single computer does not need a public address, and also it would hide these private computers from the outside world. Everyone can only see the public address, the rest is hidden behind this public address. So from the internet only the public address on the external interface of the firewall or router can be seen, and nothing beyond it.
Types of NAT
Three main types of NAT rules are used today depending on what needs to be accomplished;
Static NAT
A pool of public IP addresses are assigned to the NAT device. A private IP address can then be statically mapped to anyone of these public addresses. This type of NATTING scheme is usually used for servers requiring the same IP address always, hence the name "static", so server 1 will always have the same IP address assigned to it, server 2 will have a different public IP address assigned to it and so on.
Dynamic NAT
Again the NAT device will consist of a pool of IP addresses. This time though the pool of IP addresses will be used when needed and then given back to the pool. So if computer A needed a public address, it would take one from the pool, then hand it back when done. The next time the same computer wanted an IP address it may be assigned a different public address from the pool, because the one used previously may be in use by another computer, hence the name "dynamic". So users who want to communicate on the internet at any one time will be limited by how many public IP addresses are available in the NAT pool. A company would purchase a number of public IP's depending on their need.
Port Address Translation (PAT)
In this type of setup, a company would only have one public IP address assigned to their network, and so everyone would share this one public address when using the internet, browsing the web for example. Yes, you may be asking how can everyone share one address, well the clue lies within the name, Port address translation. When a computer wants to use the internet, the NAT device, using the PAT method will remember the IP address and source port of the internal host. For example 192.168.1.10 with a source port of 55331 wanted to browse Amazon.com. The NAT device will keep a note of this, and when Amazon replies to the public address and the port number of 55331, the NAT device will use the PAT method and look up the port information which maps to the internal computer requesting it. So it would be saying, this information Amazon has sent back to the public address and port number 55331, maps to the IP address 192.168.1.10 who originally requested it, though the information is for that computer. So the connections are uniquely identified by a source port, all using the same public IP but with unique source ports to identify who requested what information.
A company would save a reasonable amount of money and IP addresses using this method because it is only using one IP address. This has been a major factor to why IPv6 has been mentioned for some years now but still not required in most countries.
NAT is also implemented in home based routers and hardware firewalls such as the Netgear's and the Linksys of this world as well as the high end hardware firewalls such as the likes of Cisco and Juniper.
This has proved a valuable feature on hardware firewalls for saving public IP addresses and also a countermeasure for some types of attacks such as a reconnaissance attack.
Disadvantages of NAT
As with everything, NAT does have it's drawbacks. Some applications and services such as VPN and video conferencing struggle to process via NAT (Not entirely true as you can most of the time get them configured to work with NAT, but can get a little messy when setting rules up in applications,, routers and firewalls).
IPv6
However to circumvent the above issue a few extra public IP addresses can be purchased for these dedicated services. For the long run however, IPv6 is already being rolled out in some technologies and some parts of the world. This addressing scheme uses 128bit numbering scheme as opposed to IPv4's 32bits used for addresses. IPv6 supports 2 to the power of 128 addresses, compared to IPv4's 2 to the power of 32, now that is a massively huge increase of IP addresses, though future proofing the growth of IP addressing using IPv6.
Saturday 16 March 2013
Networking Interview Questions & answers
1. Define Network?
A network is a set of devices connected by physical media links. A network is recursively is a connection of two or more nodes by a physical link or two or more networks connected by one or more nodes.
2. What is a Link?
At the lowest level, a network can consist of two or more computers directly connected by some physical medium such as coaxial cable or optical fiber. Such a physical medium is called as Link.
3. What is a node?
A network can consist of two or more computers directly connected by some physical medium such as coaxial cable or optical fiber. Such a physical medium is called as Links and the computer it connects is called as Nodes.
4. What is a gateway or Router?
A node that is connected to two or more networks is commonly called as router or Gateway. It generally forwards message from one network to another.
5. What is point-point link?
If the physical links are limited to a pair of nodes it is said to be point-point link.
6. What is Multiple Access?
If the physical links are shared by more than two nodes, it is said to be Multiple Access.
7. Name the factors that affect the performance of the network?
a. Number of Users
b. Type of transmission medium
c. Hardware
d. Software
b. Type of transmission medium
c. Hardware
d. Software
8. Name the factors that affect the reliability of the network?
a. Frequency of failure
b. Recovery time of a network after a failure
b. Recovery time of a network after a failure
9. Name the factors that affect the security of the network?
a. Unauthorized Access
b. Viruses
b. Viruses
10. What is Protocol?
A protocol is a set of rules that govern all aspects of information communication.
12. What is MAC address?
Class B - 128.0.0.0 - 191.255.255.255
Class C - 192.0.0.0 - 223.255.255.255
Class D - 224.0.0.0 - 239.255.255.255
Class E - 240.0.0.0 - 247.255.255.255
49. What is NETBIOS and NETBEUI?
NETBIOS is a programming interface that allows I/O requests to be sent to and received from a remote computer and it hides the networking hardware from applications.
NETBEUI is NetBIOS extended user interface. A transport protocol designed by microsoft and IBM for the use on small subnets.
11. Define Routing?
The process of determining systematically hoe to forward messages toward the destination nodes based on its address is called routing.
12. What is MAC address?
The address for a device as it is identified at the Media Access Control (MAC) layer in the network architecture. MAC address is usually stored in ROM on the network adapter card and is unique.
13. What is the difference between TFTP and FTP application layer protocols?
The Trivial File Transfer Protocol (TFTP) allows a local host to obtain files from a remote host but does not provide reliability or security. It uses the fundamental packet delivery services offered by UDP.
The File Transfer Protocol (FTP) is the standard mechanism provided by TCP / IP for copying a file from one host to another. It uses the services offer by TCP and so is reliable and secure. It establishes two connections (virtual circuits) between the hosts, one for data transfer and another for control information.
The File Transfer Protocol (FTP) is the standard mechanism provided by TCP / IP for copying a file from one host to another. It uses the services offer by TCP and so is reliable and secure. It establishes two connections (virtual circuits) between the hosts, one for data transfer and another for control information.
14. What are major types of networks and explain?
- Server-based network: provide centralized control of network resources and rely on server computers to provide security and network administration
- Peer-to-peer network: computers can act as both servers sharing resources and as clients using the resources.
15. What are the important topologies for networks?
- BUS topology: In this each computer is directly connected to primary network cable in a single line.
Advantages: Inexpensive, easy to install, simple to understand, easy to extend. - STAR topology: In this all computers are connected using a central hub.
Advantages: Can be inexpensive, easy to install and reconfigure and easy to trouble shoot physical problems. - RING topology: In this all computers are connected in loop. Advantages: All computers have equal access to network media, installation can be simple, and signal does not degrade as much as in other topologies because each computer regenerates it.
16. What is mesh network?
A network in which there are multiple network links between computers to provide multiple paths for data to travel.
17. What is difference between baseband and broadband transmission?
In a baseband transmission, the entire bandwidth of the cable is consumed by a single signal. In broadband transmission, signals are sent on multiple frequencies, allowing multiple signals to be sent simultaneously.
18. Explain 5-4-3 rule?
In a Ethernet network, between any two points on the network ,there can be no more than five network segments or four repeaters, and of those five segments only three of segments can be populated.
19. What is multicast routing?
Sending a message to a group is called multicasting, and its routing algorithm is called multicast routing.
20.What is Proxy ARP?
It is using a router to answer ARP requests. This will be done when the originating host believes that a destination is local, when in fact is lies beyond router.
21. What is SLIP (Serial Line Interface Protocol)?
It is a very simple protocol used for transmission of IP datagrams across a serial line.
22. What is RIP (Routing Information Protocol)?
It is a simple protocol used to exchange information between the routers.
23. What is source route?
It is a sequence of IP addresses identifying the route a datagram must follow. A source route may optionally be included in an IP datagram header.
24. What is BGP (Border Gateway Protocol)?
It is a protocol used to advertise the set of networks that can be reached with in an autonomous system. BGP enables this information to be shared with the autonomous system. This is newer than EGP (Exterior Gateway Protocol).
25. What is Gateway-to-Gateway protocol?
It is a protocol formerly used to exchange routing information between Internet core routers.
26. What is NVT (Network Virtual Terminal)?
It is a set of rules defining a very simple virtual terminal interaction. The NVT is used in the start of a Telnet session.
27. What is a Multi-homed Host?
It is a host that has a multiple network interfaces and that requires multiple IP addresses is called as a Multi-homed Host.
28. What is Kerberos?
It is an authentication service developed at the Massachusetts Institute of Technology. Kerberos uses encryption to prevent intruders from discovering passwords and gaining unauthorized access to files.
29. What is OSPF?
It is an Internet routing protocol that scales well, can route traffic along multiple paths, and uses knowledge of an Internet's topology to make accurate routing decisions.
30. Expand IDEA.
IDEA stands for International Data Encryption Algorithm.
31. What is wide-mouth frog?
Wide-mouth frog is the simplest known key distribution center (KDC) authentication protocol.
33. What is Mail Gateway?
It is a system that performs a protocol translation between different electronic mail delivery protocols.
34. What is IGP (Interior Gateway Protocol)?
It is any routing protocol used within an autonomous system.
35. What is EGP (Exterior Gateway Protocol)?
It is the protocol the routers in neighboring autonomous systems use to identify the set of networks that can be reached within or via each autonomous system.
36. What is autonomous system?
It is a collection of routers under the control of a single administrative authority and that uses a common Interior Gateway Protocol.
37. What are the different type of networking / internetworking devices?
- Repeater: Also called a regenerator, it is an electronic device that operates only at physical layer. It receives the signal in the network before it becomes weak, regenerates the original bit pattern and puts the refreshed copy back in to the link.
- Bridges: These operate both in the physical and data link layers of LANs of same type. They divide a larger network in to smaller segments. They contain logic that allow them to keep the traffic for each segment separate and thus are repeaters that relay a frame only the side of the segment containing the intended recipent and control congestion.
- Routers: They relay packets among multiple interconnected networks (i.e. LANs of different type). They operate in the physical, data link and network layers. They contain software that enable them to determine which of the several possible paths is the best for a particular transmission.
- Gateways: They relay packets among networks that have different protocols (e.g. between a LAN and a WAN). They accept a packet formatted for one protocol and convert it to a packet formatted for another protocol before forwarding it. They operate in all seven layers of the OSI model.
38. What is ICMP?
ICMP is Internet Control Message Protocol, a network layer protocol of the TCP/IP suite used by hosts and gateways to send notification of datagram problems back to the sender. It uses the echo test / reply to test whether a destination is reachable and responding. It also handles both control and error messages.
39. What are the data units at different layers of the TCP / IP protocol suite?
The data unit created at the application layer is called a message, at the transport layer the data unit created is called either a segment or an user datagram, at the network layer the data unit created is called the datagram, at the data link layer the datagram is encapsulated in to a frame and finally transmitted as signals along the transmission media.
40. What is difference between ARP and RARP?
The address resolution protocol (ARP) is used to associate the 32 bit IP address with the 48 bit physical address, used by a host or a router to find the physical address of another host on its network by sending a ARP query packet that includes the IP address of the receiver.
The reverse address resolution protocol (RARP) allows a host to discover its Internet address when it knows only its physical address
.
The reverse address resolution protocol (RARP) allows a host to discover its Internet address when it knows only its physical address
.
41. What is the minimum and maximum length of the header in the TCP segment and IP datagram?
The header should have a minimum length of 20 bytes and can have a maximum length of 60 bytes.
42. What is the range of addresses in the classes of internet addresses?
Class A - 0.0.0.0 - 127.255.255.255Class B - 128.0.0.0 - 191.255.255.255
Class C - 192.0.0.0 - 223.255.255.255
Class D - 224.0.0.0 - 239.255.255.255
Class E - 240.0.0.0 - 247.255.255.255
43. What is passive topology?
When the computers on the network simply listen and receive the signal, they are referred to as passive because they don't amplify the signal in any way. Example for passive topology -linear bus.
44. What is Brouter?
Hybrid devices that combine the features of both bridges and routers.
45. What is cladding?
A layer of a glass surrounding the center fiber of glass inside a fiber-optic cable.
46. What is point-to-point protocol?
A communications protocol used to connect computers to remote networking services including Internet service providers.
47. How Gateway is different from Routers?
A gateway operates at the upper levels of the OSI model and translates information between two completely different network architectures or data formats.
48. What is attenuation?
The degeneration of a signal over distance on a network cable is called attenuation.
49. What is NETBIOS and NETBEUI?
NETBIOS is a programming interface that allows I/O requests to be sent to and received from a remote computer and it hides the networking hardware from applications.
NETBEUI is NetBIOS extended user interface. A transport protocol designed by microsoft and IBM for the use on small subnets.
Sunday 10 March 2013
Open Multiple File Formats With Single Software
- Is your Computer running too slow due to large number of applications which are installed.If you install a specific software for each file format you will end up with a lot of bloatware.It is a pain for a lot of users to install different softwares for different file formats after installing a fresh copy of their OS.You can save yourself from this trouble by installing a freeware application that is capable of opening multiple file formats (75+ formats) .
- It can give a breath of life to those systems which have low memory.Moreover it can be a lifesaver if you don’t have an idea about how to open a particular file extension, Just give it a try with Free Opener.
Supported File Formats:
- Code Files (.vb, .c, .cs, .java, .js, .php, .sql, .css, .aspx, .asp)
- Web Pages (.htm, .html)
- Photoshop Documents (.psd)
- Images (.bmp, .gif, .jpg, .jpeg, .png, .tif, .tiff)
- XML Files (.resx, .xml)
- PowerPoint Presentations (.ppt, .pptx, .pps)
- Media (.avi, .flv, .mid, .mkv, .mp3, .mp4, .mpeg, .mpg, .mov, .wav, .wmv, .3gp, .flac)
- Microsoft Word Documents (.doc, .docx)
- SRT Subtitles (.srt)
- RAW Images (.arw, .cf2, .cr2, .crw, .dng, .erf, .mef, .mrw, .nef, .orf, .pef, .raf, .raw, .sr2, .x3f)
- Icons (.ico)
- Open XML Paper (.xps)
- ML Paper (.xps)
- Torrent (.torrent)
- Flash Animation (.swf)
- Archives (.7z, .gz, .jar, .rar, .tar, .tgz, .zip)
- Rich Text Format (.rtf)
- Text Files (.bat, .cfg, .ini, .log, .reg, .txt)
- Apple Pages (.pages)
- Microsoft Excel Documents (.xls, .xlsm, .xlsx)
- Comma-Delimited (.csv)
- Outlook Messages (.msg)
- PDF Documents (.pdf)
- vCard Files (.vcf)
- EML Files (.eml)
How To Login As Admin Of Any Website
- Do you want to Admin of a website? Is this Possible? Yes! of-course it is Friends. Now this is possible with Tricks With Hacker. Today while surfing i came across a amazing but yet simple trick by the help of which you will be able to log in as the admin of any Website.
- Note -I don't take any responsibility for any harm caused due to this trick because this trick is for educational purpose only and so that if you are a webmaster or owner of a site which is using the same username and password can than you can immediately take steps to prevent unauthorized access to your site.
How To Login As Admin Of Any Website:
- Step 1). Go To Google.com and Then Search For the Following Piece of code,
- "adminlogin.asp" or "admin.asp"
- Step 2). Now Chose any website from the search results and then fill the below details in the login page,
- Username - admin
- Password - 'or''='
- Enjoy :P
- Warning- AgainI don't take any responsibility for any harm caused due to this trick because this trick is for educational purpose only.
- Hope you liked my article do share your views in the comments below.
Virtual PDF Printer

convert ur print in pdf file by using Virtual PDF Printer
Virtual PDF Printer simplifies the process of creating PDF document. Usually PDF documents are created by specific PDF composer software. However, it might be time-consuming compared with the alternative approach, which creates PDF documents from other file formats.
Virtual PDF Printer serves as a real printer to convert anything printable to PDF. The printer is a high quality PDF generator with high printing resolution, PDF document information creation, PDF content encryption with passwords protection, PDF access control, PDF scaling, PDF version and compatibility control, font embedding options and more.
Virtual PDF Printer is an affordable and effective solution offering dynamic generation of PDF documents, conversion to PDF from almost any file format and from nearly all Windows applications. The purpose of Virtual PDF Printer is to create PDF document with full options from any other file format printable with a simple click on "Printer" in Windows applications.
With Virtual PDF Printer, it is easy to create PDF documents from Word, Excel, PowerPoint, WordPerfect, Photoshop and other Windows applications. Virtual PDF Printer natively supports over 300 file formats and customers wouldn't expect anything less.
List of all RUN Commands
:- Accessibility Options : access.cpl
:- Add Hardware: hdwwiz.cpl
:- Add / Remove Programs: appwiz.cpl
:- Administrative Tools : control admintools
:- Automatic Updates: wuaucpl.cpl
:- Wizard file transfer Bluethooth: fsquirt
:- Calculator: calc
:- Certificate Manager: certmgr.msc
:- Character: charmap
:- Checking disk : chkdsk
:- Manager of the album (clipboard) : clipbrd
:- Command Prompt : cmd
:- Service components (DCOM) : dcomcnfg
:- Computer Management : compmgmt.msc
:- DDE active sharing : ddeshare
:- Device Manager : devmgmt.msc
:- DirectX Control Panel (if installed) : directx.cpl
:- DirectX Diagnostic Utility : dxdiag
:- Disk Cleanup : cleanmgr
:- System Information=dxdiag
:- Disk Defragmenter : dfrg.msc
:- Disk Management : diskmgmt.msc
:- Partition manager : diskpart
:- Display Properties : control desktop
:- Properties of the display (2) : desk.cpl
:- Properties display (tab "appearance") : control color
:- Dr. Watson: drwtsn32
:- Manager vérirficateur drivers : check
:- Event Viewer : Eventvwr.msc
:- Verification of signatures of files: sigverif
:- Findfast (if present) : findfast.cpl
:- Folder Options : control folders
:- Fonts (fonts) : control fonts
:- Fonts folder windows : fonts
:- Free Cell ...: freecell
:- Game Controllers : Joy.cpl
:- Group Policy (XP Pro) : gpedit.msc
:- Hearts (card game) : mshearts
:- IExpress (file generator. Cab) : IExpress
:- Indexing Service (if not disabled) : ciadv.msc
:- Internet Properties : inetcpl.cpl
:- IPConfig (display configuration): ipconfig / all
:- IPConfig (displays the contents of the DNS cache): ipconfig / displaydns
:- IPConfig (erases the contents of the DNS cache): ipconfig / flushdns
:- IPConfig (IP configuration cancels maps): ipconfig / release
:- IPConfig (renew IP configuration maps) : ipconfig / renew
:- Java Control Panel (if present) : jpicpl32.cpl
:- Java Control Panel (if present) : javaws
:- Keyboard Properties: control keyboard
:- Local Security Settings : secpol.msc
:- Local Users and Groups: lusrmgr.msc
:- Logout: logoff
:- Microsoft Chat : winchat
:- Minesweeper (game): winmine
:- Properties of the mouse: control mouse
:- Properties of the mouse (2): main.cpl
:- Network Connections : control NetConnect
:- Network Connections (2): ncpa.cpl
:- Network configuration wizard: netsetup.cpl
:- Notepad : notepad
:- NView Desktop Manager (if installed): nvtuicpl.cpl
:- Manager links: packager
:- Data Source Administrator ODBC: odbccp32.cpl
:- Screen Keyboard: OSK
:- AC3 Filter (if installed) : ac3filter.cpl
:- Password manager (if present): Password.cpl
:- Monitor performance : perfmon.msc
:- Monitor performance (2): perfmon
:- Dialing Properties (phone): telephon.cpl
:- Power Options : powercfg.cpl
:- Printers and Faxes : control printers
:- Private Character Editor : eudcedit
:- Quicktime (if installed) : QuickTime.cpl
:- Regional and Language Options: intl.cpl
:- Editor of the registry : regedit
:- Remote desktop connection : mstsc
:- Removable Storage: ntmsmgr.msc
:- requests the operator to removable storage: ntmsoprq.msc
:- RSoP (traduction. ..) (XP Pro): rsop.msc
:- Scanners and Cameras : sticpl.cpl
:- Scheduled Tasks : control schedtasks
:- Security Center : wscui.cpl
:- Console management services: services.msc
:- shared folders : fsmgmt.msc
:- Turn off windows : shutdown
:- Sounds and Audio Devices : mmsys.cpl
:- Spider (card game): spider
:- Client Network Utility SQL server : cliconfg
:- System Configuration Editor : sysedit
:- System Configuration Utility : msconfig
:- System File Checker (SFC =) (Scan Now) : sfc / scannow
:- SFC (Scan next startup): sfc / scanonce
:- SFC (Scan each démarraget) : sfc / scanboot
:- SFC (back to default settings): sfc / revert
:- SFC (purge cache files): sfc / purgecache
:- SFC (define size CAHC x) : sfc / cachesize = x
:- System Properties : sysdm.cpl
:- Task Manager : taskmgr
:- Telnet client : telnet
:- User Accounts : nusrmgr.cpl
:- Utility Manager (Magnifier, etc) : utilman
:- Windows firewall (XP SP2) : firewall.cpl
:- Microsoft Magnifier: magnify
:- Windows Management Infrastructure: wmimgmt.msc
:- Protection of the accounts database: syskey
vWindows update: wupdmgr
:- Introducing Windows XP (if not erased) : tourstart
:- Wordpad : write
:- Date and Time Properties : timedate.cpl
:- Add Hardware: hdwwiz.cpl
:- Add / Remove Programs: appwiz.cpl
:- Administrative Tools : control admintools
:- Automatic Updates: wuaucpl.cpl
:- Wizard file transfer Bluethooth: fsquirt
:- Calculator: calc
:- Certificate Manager: certmgr.msc
:- Character: charmap
:- Checking disk : chkdsk
:- Manager of the album (clipboard) : clipbrd
:- Command Prompt : cmd
:- Service components (DCOM) : dcomcnfg
:- Computer Management : compmgmt.msc
:- DDE active sharing : ddeshare
:- Device Manager : devmgmt.msc
:- DirectX Control Panel (if installed) : directx.cpl
:- DirectX Diagnostic Utility : dxdiag
:- Disk Cleanup : cleanmgr
:- System Information=dxdiag
:- Disk Defragmenter : dfrg.msc
:- Disk Management : diskmgmt.msc
:- Partition manager : diskpart
:- Display Properties : control desktop
:- Properties of the display (2) : desk.cpl
:- Properties display (tab "appearance") : control color
:- Dr. Watson: drwtsn32
:- Manager vérirficateur drivers : check
:- Event Viewer : Eventvwr.msc
:- Verification of signatures of files: sigverif
:- Findfast (if present) : findfast.cpl
:- Folder Options : control folders
:- Fonts (fonts) : control fonts
:- Fonts folder windows : fonts
:- Free Cell ...: freecell
:- Game Controllers : Joy.cpl
:- Group Policy (XP Pro) : gpedit.msc
:- Hearts (card game) : mshearts
:- IExpress (file generator. Cab) : IExpress
:- Indexing Service (if not disabled) : ciadv.msc
:- Internet Properties : inetcpl.cpl
:- IPConfig (display configuration): ipconfig / all
:- IPConfig (displays the contents of the DNS cache): ipconfig / displaydns
:- IPConfig (erases the contents of the DNS cache): ipconfig / flushdns
:- IPConfig (IP configuration cancels maps): ipconfig / release
:- IPConfig (renew IP configuration maps) : ipconfig / renew
:- Java Control Panel (if present) : jpicpl32.cpl
:- Java Control Panel (if present) : javaws
:- Keyboard Properties: control keyboard
:- Local Security Settings : secpol.msc
:- Local Users and Groups: lusrmgr.msc
:- Logout: logoff
:- Microsoft Chat : winchat
:- Minesweeper (game): winmine
:- Properties of the mouse: control mouse
:- Properties of the mouse (2): main.cpl
:- Network Connections : control NetConnect
:- Network Connections (2): ncpa.cpl
:- Network configuration wizard: netsetup.cpl
:- Notepad : notepad
:- NView Desktop Manager (if installed): nvtuicpl.cpl
:- Manager links: packager
:- Data Source Administrator ODBC: odbccp32.cpl
:- Screen Keyboard: OSK
:- AC3 Filter (if installed) : ac3filter.cpl
:- Password manager (if present): Password.cpl
:- Monitor performance : perfmon.msc
:- Monitor performance (2): perfmon
:- Dialing Properties (phone): telephon.cpl
:- Power Options : powercfg.cpl
:- Printers and Faxes : control printers
:- Private Character Editor : eudcedit
:- Quicktime (if installed) : QuickTime.cpl
:- Regional and Language Options: intl.cpl
:- Editor of the registry : regedit
:- Remote desktop connection : mstsc
:- Removable Storage: ntmsmgr.msc
:- requests the operator to removable storage: ntmsoprq.msc
:- RSoP (traduction. ..) (XP Pro): rsop.msc
:- Scanners and Cameras : sticpl.cpl
:- Scheduled Tasks : control schedtasks
:- Security Center : wscui.cpl
:- Console management services: services.msc
:- shared folders : fsmgmt.msc
:- Turn off windows : shutdown
:- Sounds and Audio Devices : mmsys.cpl
:- Spider (card game): spider
:- Client Network Utility SQL server : cliconfg
:- System Configuration Editor : sysedit
:- System Configuration Utility : msconfig
:- System File Checker (SFC =) (Scan Now) : sfc / scannow
:- SFC (Scan next startup): sfc / scanonce
:- SFC (Scan each démarraget) : sfc / scanboot
:- SFC (back to default settings): sfc / revert
:- SFC (purge cache files): sfc / purgecache
:- SFC (define size CAHC x) : sfc / cachesize = x
:- System Properties : sysdm.cpl
:- Task Manager : taskmgr
:- Telnet client : telnet
:- User Accounts : nusrmgr.cpl
:- Utility Manager (Magnifier, etc) : utilman
:- Windows firewall (XP SP2) : firewall.cpl
:- Microsoft Magnifier: magnify
:- Windows Management Infrastructure: wmimgmt.msc
:- Protection of the accounts database: syskey
vWindows update: wupdmgr
:- Introducing Windows XP (if not erased) : tourstart
:- Wordpad : write
:- Date and Time Properties : timedate.cpl
Registred your IDM Manually for lifetime.
- Hello Friends, Using this hack you can register the Internet Download Manager (IDM) for free using you own credentials i.e register on your Name and email ID.
- I am explaining the manual hacking method because most of my users said that patch and keygen contain viruses. This hack also works for trail IDM that means download a trail IDM from there site and register the professional i.e. full version of IDM with your credentials for free using my hack.
Hack or crack IDM manually:
- Step 1: Download the IDM trial or If you already have IDM installed Update it by going to Help---}} then to check for Updates.
- Step2: Now Go to START => Then go to RUN and type the following text and click enter:
- notepad %windir%\system32\drivers\etc\hosts
- Step3: Now right click on hosts file and go to its properties, then go to security tab and then select your admin account, just below u will see an edit button (in front of change permissions), Now give the user full control and write and read rights and then click on apply and then click on Ok, now u will be able to edit the hosts file and save changes in it.
Detail Note about Granting Permission In Windows7:
- For Windows 7 users, due to security reasons you will not be able to save hosts file.so follow this steps : First of all go to C:/ drive then go to Windows Folder and then go to System32 folder and then go to Drivers folder and then go to Etc Folder, in the Etc folder you will see the hosts file.
- Now right click on hosts file and go to its properties then go to Security tab select Users under Group or user names and click on edit button,Permission For Host Window will get open, in that window select Users account and grant permission in bellow section which is "Permission for SYSTEM" by clicking all checkbox under "Allow" Name and press Ok.Dnt click on any Deny check box.
- Note: If you have login through admin then skip this step6 .Its just for granting permission for editing file.
- Step4: Now a notepad file appears something like this as shown below:
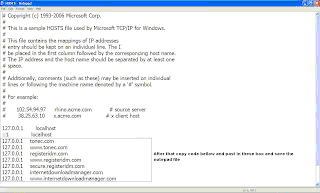
- Now copy the below lines of code and add to hosts file as shown above image box :
- 127.0.0.1 tonec.com
- 127.0.0.1 www.tonec.com
- 127.0.0.1 registeridm.com
- 127.0.0.1 www.registeridm.com
- 127.0.0.1 secure.registeridm.com
- 127.0.0.1 internetdownloadmanager.com
- 127.0.0.1 www.internetdownloadmanager.com
- 127.0.0.1 secure.internetdownloadmanager.com
- 127.0.0.1 mirror.internetdownloadmanager.com
- 127.0.0.1 mirror2.internetdownloadmanager.com
- After adding these piece of code, save the notepad file. And exit from there.
- Step5: Now open IDM and click on Registration. When you click on registration, Now a new dialog(window) appears that is asking for Name, Last Name, Email Address and Serial Key.
- Step6: Now Enter you name, last name, email address and in field of Serial Key enter any of the following Keys:
- RLDGN-OV9WU-5W589-6VZH1
- HUDWE-UO689-6D27B-YM28M
- UK3DV-E0MNW-MLQYX-GENA1
- 398ND-QNAGY-CMMZU-ZPI39
- GZLJY-X50S3-0S20D-NFRF9
- W3J5U-8U66N-D0B9M-54SLM
- EC0Q6-QN7UH-5S3JB-YZMEK
- UVQW0-X54FE-QW35Q-SNZF5
- FJJTJ-J0FLF-QCVBK-A287M
- And click on ok to register.
- Step7: After you click ok, it will show an message that you have registered IDM successfully.
- Now start your Internet download manager, and now you IDM has been converted to full version and specially when you update next time, your registration will not expire.
- That means it will remain full version for life time and you can update it without any problem in future.
Proof of Successfully Hacking IDM:
- Note: To update idm you have to remove those websites added in the host file, after removing those website,save that Hosts file and update IDM software. After succesfull updation again follow above steps to crack Internet Download manager.
- I hope you are now able to convert your Trial version of IDM into Full Version. If you have any problem in this tutorial on Hack and Crack IDM,
- please mention it in comments. Enjoy.....
Tuesday 8 January 2013
InterView Questions and Answer
Q1. What is Operating System. ?
Ans. Operating System work as an interpreter between computer hardware and application Operating System work as a user interface.
Q2. Type of Operating System.?
Ans. There are two type of Operating System :
1. SOS - Simple Operating System as for example:- Windows 95,98,ME
2. NPS - Network Operating System as for example:- Windows NT,200,2003
Q3. What is Server .?
Ans. Server are computer that provides that service. As for Example -
1. DNS Server Domain naming system
2. WINS Server Window naming system
3. DHCP Server
4. RAS Server
5. VPN Server
Q4. What is RAS Server. ?
Ans. RAS stands for Remote Access Server. It is basically use for mobile user in the network. This Server provides the remote access connectivity for mobile user. In this way all of the mobile users are connected to server through telephone line. This Server also provides the connectivity between two or more Offices in the Network.
Q5. What is VPN Server. ?
Ans. VPN stands for Virtual Private Network . It is basically use for mobile user in the network . This Server provides the remote access connectivity for mobile user. In this way all of the mobile users are connected to server through Internet. This is service also provides the connectivity between two or more Office in the Network. VPN is cost Effective (No costly).
Q6. What is IAS Server. ?
Ans. IAS stands for Internet Authentication Services. IAS Server is also known as RADIUS Server. IAS Server Provides the centralized management of multiple RAS & VPN Servers in the Network. On this Server Remote Access policy and Remote Access Logging Options are available.
Q7. Difference Between FAT & NTFS.?
Ans. There are major difference are available between FAT & NTFS File Systems such as.
The overall structure of any operating system where file are named, modified and executed is called file system.
FAT NTFS
--Fat stands for File Allocation Table. --NTFS stands for New Technology File System.
--There are two categories in Fat file systems: --There are three categories in NTF File System:
1. Fat 16 1.NTFS 4.0 - NT O/S
2. Fat 32 2.NTFS 5.0 - 2000 O/S
3. 3.NTFS 6.0 - 2003 O/S
--In Fat Up To Folder Level Security is available. --In NTFS UP-to File Level Security is Available.
--Compression Option is not available. --Compression Option is available.
--Encryption Option is not available. --Encryption Option is available.
--Disk Quota Option is not available. --Disk Quota Option is available.
--FAT Supported By All of The Microsoft Based --TFS Supported By only Limited Microsoft Based
Operating System. Operating System.
Q8. What is Active Directory.?
Ans. Active Directory is the main concept of Windows 2000/20003 Network. It stores all of the information about the whole network such as users,printers,computers etc.
Q9. What is Tree. ?
Ans. A group of domain is called tree and sharing a contiguous Name space.
Q10. What is Forest. ?
Ans. A goup of tree is called forest and does not sharing a contiguous name space but sharing a common configuration (schema).
Q11. Difference between D.C. And A.D.C. ?
Ans. D.C. Stands for Domain Controller and A.D.C. Stands for Additional Domain Controller. AD.C is a back up copy of D.C Only one difference is available Between D.C. And A.D.C. I.e.-Operation Master Role. On D.C. All of the three Operating Master Roles are available--
1. RID Master
2. PDC Emulator
3. Infrastructure Operation Master Role.
But on A.D.C. No any Operation Master roles are available
Q12. What is benefits of Child Domain. ?
Ans. There are many benefits of Child Domain Such As---
1. Security Boundary
2. Administrative Overhead Low
3. Network Traffic Low
Q13. What is Group.?
Ans. Group is collection of user account. It provides the simplified administration in the network.
Q14. What is OU.?
Ans. OU stands for Organization Unit. On OU we define goup policy in the network . Group policy is basically assigned on active directory container i.e.. Site ,Domain, OU. When ever we want some users in the network do not use shut down the system, do not use run command, do not use control panel, then we put that user in the OU and assign the appropriate Group Policy on that OU.
Q15. What is Group Policy.?
Ans. Group policy provides the stream line access to all fo the users in the network. Group policy is basically assigned on active directory container.i.e Site ,Domain, OU. When ever we want some users in the network do not use shut down the system, do not use run command, do not use control panel, then we put that user in the OU and assign the appropriate Group Policy on that OU.
Q16. Difference between permission, Right and Policy./
Ans. Permission - Permission are basically on network resources as for example--File,Folder.share Folder. Printer.
Right - Right is basically assign to users and groups.
Policy - Policy are basically assigned active directory container i.e.- Site, Domain ,OU.
Q17. What is ISA Server. ?
Ans. ISA stands for internet Security Acceleration. ISA Server Provides the Internet connectivity for all of the users in network ISA server also works as a Proxy Server in the network. With the help of ISA Server Administrator can Filtering a Client request For a Specific Web site in the Network.
Q18. What is Default Gateway. ?
Ans. Default Gateway is the IP Address of Router in the Network. When ever any clients want to go to another network that query will forward to Default Gateway.
Q19. What is Site.?
Ans. A Site is a geographical area where all of the domain available. Site manages the Replication Traffic between Two or More Difference Sites in the Network.
Q20. What is Operation Master Roles.?
Ans. Operation Master Role is available on Domain Controller in the Network. There are Five type of Operation Master Role :-
1. Schema Master
2. Domain Naming Master
3. RID Master
4. PDC Emulator
5. Infrastructure Operation Master Role
Q21. Difference between Mixed Mode and Native Mode. ?
Ans. There are three type of domain mode:-
1. Mixed Mode -- In this node NT,win2kand win 2k3 D.C are available.
2. Win 2k Native Modes --In this mode Win 2k and win 2k3 D.C. Are available.
3. Win 2k3 Native Mode -- In this mode only win 2k3 D.C. Are available.
Q22. What is SCSI.?
Ans. SCSI stands for Small Computer System Interface. In SCSI the rate of date transmission is fast SCSI Hard Disk speed - R.P.M is fast In SCSI Date Transmission Speed is 320 MBPS in the Network. In SCSI Controller We can Connect Maximum 15 physical Devices in the system.
Q23. What is Host Record and PTR Record. ?
Ans. A record is also called host record. This record is basically created in forward lookup Zone. PTR record is also called pointer record. This record is basically created in reverse Lookup Zone.
Q24. What is Reservation. ?
Ans. Reservation is basically used in DHCP Server. When Ever we want This Computer is always received This IP Address From DHCP Server in The Network, in that Case we create a Reservation in DHCP Server of that particular Computer in The Network.
Q25. IP Address Range/Classes. ?
Ans. There are two type of IP address:-
1.Class Full IP address.
2.Class Less IP address.
Class Full IP Address : There are Five Classes :-
I. Class A - 0 - 126 (127 is reserved for Loop back)
II. Class B - 128 - 191
III. Class C - 192 - 223
VI. Class D - 224 - 239
V. Class E - 240 - 225
Q26. Difference between Hardware Router and Software Rother. ?
An.. Hardware Router - Hardware Router is a dedicated Router. It having a lot of features Such as Security,dedicated routing in the network. As for Example Cisco Router.
Software Router - Soft ware Router is not a dedicated Router.It provides the difference ------ also. Such as DNS server. i.e-- Window Based Router.
Q27. Difference Between Hardware firewall and Software firewall.?
Ans. Hardware Firewall - It is dedicated firewall . A lost of security features are available on Hardware based firewall. AS for example - Cisco pix firewall.
Software Firewall - It is not dedicated firewall. It provides the normal security in the network -- cheek Point.
Q 28. What is Domain Controller. ?
Ans. D.C. Stands for Domain Controller. It provides the centralized management of entire domain in the network . When ever we will install active directory database on a server side operating system then after that system becomes a D.C. Domain Controller manages all security related interaction between users and computer in the Network.
Q 29. What is B Router .?
Ans. B Router stands for Bridge Router. We can say this is a layer three bridge that provides the communication between two or more difference Network ID.
Q30. What is Bridge.?
Ans. Bridge is a layer 2 Network device that provides the communication within the same network ID> IN bridge Maximum16 Port are available.
Q31. Difference Between Gateway and Router. ?
Ans. Router works on some network architecture but Gateway works on different network architecture.
Q32. What is POP Server/SMTP Server. ?
Ans. POP stands for Post office Protocol. It is basically use for mail receiving purpose in the network.
SMTP stands for Simple Mail Transfer Protocol. It is basically user for sending a mail as well as receiving a mail in the network.
Q33. What is active directory Partitions. ?
Ans. Active Directory Partition is a Logical Partition of Active Directory. This Partition is Basically Use for Replication form D.C. to A.D.C & D.C.to G.C.S (Global Catalog Server) in the Network. There are three Type of Active Directory Partition :
1. Schema Partition
2. Configuration Partition
3. Domain Partition
Q 34. Type of Active Directory Partition. ?
Ans. There are three type of Active Directory Partition :
1. Schema partition
2. Configuration partition
3. Domain partition
Q35. What is Function of Ping Command.?
Ans. Ping provides to check the physical IP Connectivity between two or more device in the network. Ping Sends an ICMP request form source computer to destination computer and destination computer sends an ICMP reply.
Q36. What are Broadcasting, Multicasting, Unicasting. ?
Ans. Broadcasting -- One All
Multicasting -- One to Many Not All
Unicasting -- One to One
Q37. What is Group Nesting .?
Ans. When we add two or more Groups within a Single Group. It is called Group Nesting.
Q38. What is FIXMBR. ?
Ans. FIXMBR Repair the Master boot Record of the Partition Boot Sector.
Q39. What is FIXBOOT.?
Ans. FIXBOOT write a new Partition Boot sector on to the system partition.
Q40. What is SID. ?
Ans. SID stands for Security Identifier, Every Object has a unique ID. It is called SID.
Q41. What is RADIUS Seres. ?
Ans. RADIUS Stands for Remote Authentication Dail-in User Service. RADIUS Server provides the Centralized management of Multiple RAS & VPN Server in the Network. On this Server Remote Access Policy and Remote Access Logging Options are available.
Q42. What is Trusting Domain. ?
Ans. In Trusting Domain Resources are available.
Q43. What is Trusted Domain. ?
Ans. In Trusted Domain User Account's are Available.
Q44. What is Microsoft Exchange Server.?
Ans. Microsoft Exchange Server is Software that provides the service such as sending & receiving mail.
Q45. What is printer. ?
Ans. Printer is Software that Governing the print Device .There are two type of printer. :
1. Local Printer
2. Network Printer
Q46. What is chatting. ?
Ans. Chatting is real time Conversion between two or more peoples in the Network.
Q47. What is Directory Service Restore Mode. ?
Ans. When our Active Directory Database is not Working Properly, Then we Restart the Domain Controller and press F8 key after Selecting the Directory Services Restore Mode and then after Restoring the Active directory database from the Last Backup.
Q48. What is normal Backup. ?
Ans. Just like a normal backup By default backup.
Q49. What is incremental Backup. ?
Ans. In Incremental backup only incremental parts are backup not full backup.
Q50. What is Differential Backup. ?
Ans. In Differential Backup we take full backup after normal backup.
Q51. What is Packet.?
Ans. A Packet is a logical Grouping of information that includes a header which contains location information and user data.
Q52. What is Forwarder. ?
Ans. It is basically use in DNS Server. When client Query to the DNS Server. In that case if the DNS is having a best result then DNS sever give the best result to the Client Computer in the Network otherwise DNS Server forward the query to the root DNS Server on own behalf and give the complete result to the client computer in the network.
Q53. What is encryption. ?
Ans. There are Four Type of Encryption :
1. No Encryption -- NO
2. Basic -- MPPE -- 40 bits -- des
3. Strong -- 56 bits -- des -- MPPE/IPSec.
4. Strongest -- 128 bit date encryption -- MPPE/IPSec
Q54. What is Rip V.1, Rip V.2, IGMP, OSPF.?
Ans. 1.Rip V.1 -- Broadcast -- Small Network Use.
2.Rip V.2 -- Multicast
3. IGMP -- Multicast
4. OSPF -- Multicast - For Larger Network
Q55. What is the requirement Of VPN Server.?
Ans. VPN require IP connectivity between the client and the server. VPN does not require a dial up connection Between the client and server in the Network.
Q56. What is inbound Connection .?
Ans. Inbound Connection is Created on server side.
Q57. What is outbound Connection.?
Ans. Outbound Connection is created on client side.
Q58. What is the function of jetpack command in DHCP Server. ?
Ans. Check the database consistency of DHCP Server in the network.
Q59. What is Remote Access Policy. ?
Ans. In Remote Access policy there are three options are available:-
1. Condition - 8 a.m. To 5 p.m. Marketing Group
2. Permission - Yes/No
3. Profile - Connectivity time, IPSec Policy
Q60. What is TRACERT .?
Ans. TRACERT display computer route information form source computer to destination computer in the network.
Q61. What is the function of jetpack command in WINS Server. ?
Ans. For Compacting the WINS database we use jetpack command.
jetpack wins,mdb kk. Mdb
Q62. What is tunneling form.?
Ans. The sending and receiving fo data through a secure way in the network, it is called tunneling form.
Q63. What is trust relationship.?
Ans Trust Relationship is an important part in the client server network. There are tow types of Trust relationship :-
1. Non Transitive Trust - Non Transitive Trust is a one way trust relationship in the network. As for Example -- in NT Network.
2. Transitive Trust - Transitive Trust is tow way trust relationship in the network. As for example --in 200/2003 Network.
Q64. What is DACL.?
Ans DACL stand for Discretionary Access Control List. in DACL basically permission entry is available of any user in the Network.
Q65. What is SACL.?
Ans. SACL stand for system Access Control List. In SACL basically auditing Entry is available of any user in the network.
Q66. What is MSI.?
Ans. This file is basically use for deploying or installation of any application in the network.
Q67. What is MST.?
Ans. The file is basically using for repairing of any application in the network.
Q68. What is Zap File.?
Ans. It is basically use for that application, Which do not have the MSI file. We Create a text file with zap extension for deploying or installation purpose of any application in the network.
Q69. What is ACE.?
Ans. ACE stand for access control Entry.
Q70. What is operation master role. ?
Ans. Operation master role is available on domain controller in the network.
There are five type of operation master role inside the active directory :-
1. Schema master - Schema master is responsible for changes of schema, updating of schema in the network.
2. Domain Naming Master - Domain naming Master is responsible for adding or removing a domain inside the forest.
3. RID Master - RID Master Provides RID no of each D.C. In the network. Every D.C. Is having a one ID no, It is called RID NO Domain, Object -- S.I.D.
4. PDC Emulator - It is basically use for previous version of windows 2000 clients in the Network.
PDC emulator work as an emulator for previous version of windows2000 client in the network.
PDC - Primary Domain Controller
BDC - backup Domain Controller
5. Infrastructure Operation Master - infrastructure Operation Master Role provides uniqueness of any object inside the forest. Infrastructure operation master role. Updates references to objects and goup membership from other domain in the network.
Q71. What is dedicated Server. ?
Ans. A dedicated server functions as a server only not as a client. As for Example-- Domain Controller.
Q72. What is bridgehead Server. ?
Ans. A bridgehead server is a central point in the site that is responsible for replication form another Site.
Q73. What is the booting file Of Windows 2000, 2003, XP OS.?
Ans. 1. NTLDR
2. NTDETECT.COM
3.BOOT.INI
4.NTBOOTDD.SYS
5.NTOSKRNL.EXE
Q74. What is clustering. ?
Ans. Suppose, I create a web site -- www.yahoo.com. This same web page is available On all of the ten computers. I configured clustering on all of the ten computer. Let say at a same time one thousand people access this web services are provided by only one computer, then it may be a very busy. But in this time workload is sharing among ten computers. This is called clustering and if one server will be down server are providing the services in the network . There are tow benefits of Clustering :-
1. Fault Tolerance
2. Load Balancing
Q75. What is authoritative restore. ?
Ans. In this process the one lacks version no high of each object in active directory database and this parts is overrides on other D.C. In the network. We will use this method in Following options such As-- some deletions. Some rename.
Q76. What is migration. ?
Ans. It is basically use for converting NT, 2000 network 2003 network. There are two types of migration :-
1. Upgrading -- in upgrading process maintains current domain model. As for Example-l Before migration three domains are available and after migration again three domain are available.
2. Restructuring -- In restructuring Process no maintain domain models. As for example- Before migration three domains are available and after migration may be one domain will be available.
Q77. What is Schema. ?
Ans. Schema basically reads the Attributes and defines the classes. Such as User class, Printer class,computer class.
Q78. What is Sub Zone. ?
Ans. STUB Zone is a pointer Record of Sub Child Domain in the Network. STUB Zone provides the directly communication between parent Domain and Sub child Domain. If any case middle level DNS will down in that case parent and sub child domain are still communicating with each other in the network.
Q79. What is Shadow Copy. ?
Ans. Shadow copy provides the automatic backup of any particular shared Folder in the Network .Shadow copy provides the No. Of previous version Backup of any particular Shared folder in the Network. In any time we can view and restore of any previous version backup of the particular Folder. This is the new feature of windows 2003 Operating System.
Q80. What is RSOP. ?
Ans. RSOP stands for Resultant Set of Policy. It is basically use for, when ever we want, What ever the effective policy is apply on a particular user and particular computer in the Network.
Q81. What is Goup Policy Modeling. ?
Ans. In Goup policy Modeling. We can find out what ever the effective policy is apply on a particular user and particular computer in the network.
Q82. What is Goup Policy Resulting.?
Ans. In Goup policy resulting, we can find out what ever the effective policy is apply on a particular user and particular computer in the network.
Q83. What is SUS Server.?
Ans. SUS stands for Software update server. This server provides the Automatic Updating from Microsoft update server to all of the clients and servers in the network.
Q84. What is Windows update. ?
Ans. Window update Server provides the automatic updating form Microsoft Windows update server to all of the Client & Server in the network.
Q85. What is GPMC. ?
Ans. GPMC stands for Goup policy Management console. With the help of this Tools We manage the Goup policy object of entire Forest from single location in the network. With the help of this Tools we also take the backup and restoring of Goup policy object.
Q86. What is Conditional Forwarding. ?
Ans. Conditional Forwarding is Basically use in DNS server. In DNS server, We define the condition, If any DNS Query is Related to that particular Domain. In that case that Query will directly forward to that domain and if that DNS Query is not Related to that particular Domain in that case that quey will Forward to ISP DNS server in the network. With the help of conditional Forwarding, we can say the rate of Date Transmission Rate is Fast in the network this is the new Features in Windows 2003 Operating System.
Q87. What is Effective Permission. ?
Ans. Effective Permission display that is what ever the effective permission is available of any user in any particular resources in the Network.
Q88. What is the Booting file of 98 Operating System .?
Ans. 1. MSDOS.SYS
2. IO.SYS
3.COMMAND.COM
Q89. What is ASR.?
Ans. ASR stands for automatic System Recovery, ASR provides the complete backup of any computers in the network.
Q90. What is difference between system policy and Goup policy.?
Ans. System Policy are used in NT environment But Goup policy are used in windows 2000and windows 2003 environment.
Q91. What is connection oriented Protocol. ?
Ans. Before the Data is Sending from source computer to destination computer in the network first of all connection is establish between source to destination computer. It is called connection oriented Protocol . AS for Example:- TCP.
Q92. What is IDE. ?
Ans. IDE stands for Integrated Device Electronics. In IDE we can connect maximum 4 physical devices in the system. In IDE the rate of data Transmission is slow. In IDE Maximum speed is 80 MBPS in the Network.
Q 93. Why we crate a Site. ?
Ans. There are many benefits for creating a Site inside the Network Such as.
1. Manage Replication Traffic Inside the network.
2. For Goup Policy purpose.
3. Administrative Burden Will be low.
4. Network Performance will be good Logon Traffic.
5. Reduce the No. Of request for Global Catalog Server.
Q94. Difference between IP V-4 and IP V-6. ?
Ans. There are major Difference between IP V-4 and IP V-6 Such Aa :-
1. In IP V-4 is a 32bits IP Address But IP V-6 128 bits IP Address.
2. IP V-4 is Decimal Format. But IP V-6 is Hexa-Decimal Number.
3. IP V-4 has 4 Octets. But IP V-6 has 16 Octets.
4. IP V-4 is supported by operating System But IP V-6 Supported by only some Operating System.
5. In IP V-4 only limited number of IP Address are available But in IP V-6 a Number of IP Address are available.
Q95. What is the Function of Schema Partition. ?
Ans. Schema Partition is Responsible for Replication to all of the Domains inside the Forest.
Q 96. What is the function of Configuration Partition. ?
Ans. Configuration Partition is responsible for replication to all of the Domains inside the Forest.
Q97. What is the function of Domain partition. ?
Ans. Domain Partition is responsible for Replication to all of the Additional Domain Controller inside the Own Domain.
Q98. What is Active Directory Database Location ?
Ans. System-root\NTDS Folder \NTDS.DIT.
Subscribe to:
Posts (Atom)





























